
 |
|
 |
|
Back to Article List SplitDNS Can Add Security and Speed to a Website By Laura Taylor and Wayne Periman August 10, 2000 Can a firewall slow down HTTP proxies? If it is being used as a VPN (Virtual Private Network) endsite, and is performing encryption algorithms, the answer is yes. Though proxy firewalls have come a long way, and can be as fast as stateful packet inspection firewalls if engineered efficiently, they too have also been known to suffer performance problems depending upon what they're being used for. Putting a DNS server both inside and outside your firewall -- a technique called "split DNS" -- can give your website a performance boost, however, the key benefit is the added security of not allowing external users the ability to "see" inside the network. Okay, so you've decided to see what split DNS can do for your website, and now you're ready to implement it. There are many ways to implement split DNS, but we'll examine only one particular paradigm. The implementation can be done using either UNIX or NT; however care should be taken to "harden" the operating system no matter which one is used. Put one DNS server inside your firewall, and one DNS server on your security perimeter, outside your firewall. Figure 1. A split DNS architecture. 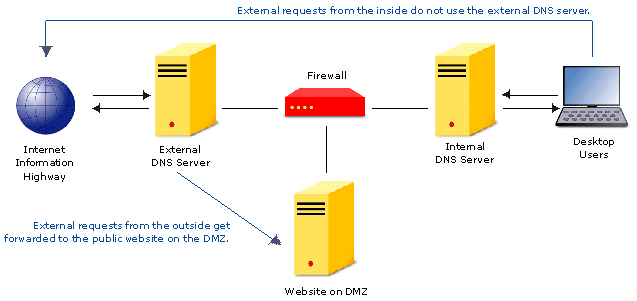 Your internal DNS server should resolve only queries from inside your network, not those from the general Internet at large. You don't want Internet cybervandals to poison your internal DNS cache, so you don't let your internal DNS server respond to external queries. Your external DNS server should resolve cached DNS queries that point to your protected websites. The external DNS server holds the publicly addressable entities for your corporation's domain. Inbound queries from the Internet are filtered so that they are only allowed to find your organization's publicly addressable URLs. It is possible for your internal desktop users to use the external DNS server for publicly resolvable addresses out on the Internet, but then they will be putting a load on your external DNS server, competing with your customers for CPU cycles. Since the goal is to make your customers experience a fast website, don't setup your internal DNS server to be a slave of your external DNS server. Instead, use an altogether different server on your internal network for a secondary DNS slave. Set up your secondary DNS slave (not shown on the above diagram) to resolve outbound queries to other domains, and your internal DNS primary to resolve queries for your own local corporate domain. In this configuration, your internal slave DNS server is allowed to "help out" your internal primary DNS server, but your external DNS server is not allowed to "help out" your internal DNS server. Remember, we are trying to optimize performance for customers (not for your internal corporate users; that's another project for a later date). Let's say one of your local corporate users queries website A. The query goes to your internal DNS server. Your internal DNS server determines that it is not authoritative for website A. DNS zone, and forwards the request to the internal slave DNS server, which responds to the internal primary DNS server, which forwards the response back to the user. When the external DNS server recognizes a customer query from the Internet, it performs the public DNS lookup as usual, finding the site through its client mappings to the Internet root DNS servers. When the external DNS server receives the response, it forwards the request to the website, which in turn returns it to the requesting customer's desktop, via the Internet. If you put BIND on the firewall, you can put the functionality of the external DNS server on the firewall, which is a way to achieve the same transaction, with one fewer servers. You would set up your proxy on the firewall to only allow DNS traffic on TCP port 53 and UDP port 53. The firewall would run a copy of BIND and act as the external DNS resolver. Outside Internet addresses could then allow DNS traffic to and from the firewall's address, and from there to the website. User Reminders: There are a few tricky points in implementing split DNS. This checklist should help you avoid problems:
|
| Copyright 1997-2023 Relevant Technologies. All rights reserved | Legal and Privacy | Sitemap Email: info@relevanttechnologies.com | 8115 Maple Lawn Blvd, Suite 350, Fulton, MD 20759 |